Introduction
In the constantly evolving digital landscape, data breaches have become both a frequent and highly concerning occurrence. One of the latest incidents to catch the attention of cybersecurity professionals and curious observers alike involves TheJavaSea.me and a mysterious leak known as AIO-TLP370. While at first glance the name might sound like a random code, the truth is far more complex. This breach appears to involve sensitive technical resources, potentially impacting software security, enterprise networks, and even government-linked systems.
What Is AIO-TLP370?
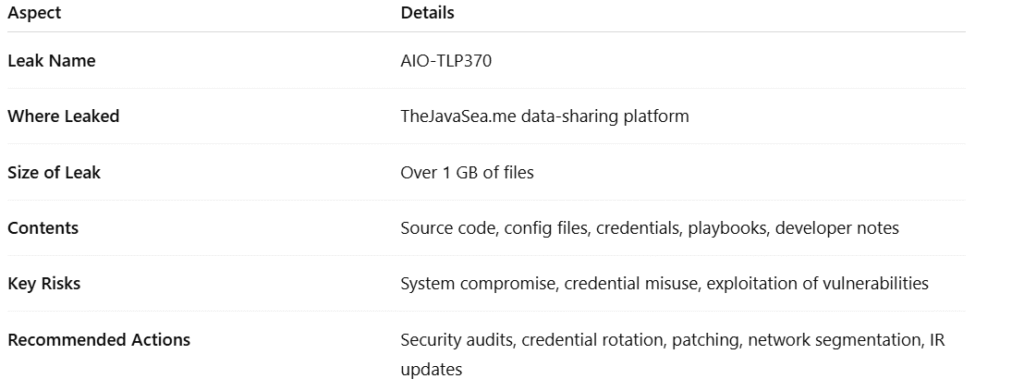
AIO-TLP370 is believe to be a sophisticated All-In-One Transparent Log Processor, a system designed to manage, store, and analyze massive amounts of log data from various networks and devices. Such systems are often use by large corporations, cybersecurity agencies, and high-level IT departments.
The “TLP” portion of the name may refer to the Traffic Light Protocol, a classification system for handling sensitive information, ranging from public (TLP:WHITE) to highly confidential (TLP:RED). The “370” could indicate a version, an internal project code, or a release identifier.
Given its potential capabilities, any leak of AIO-TLP370-related files could reveal operational secrets, security measures, and vulnerabilities.
The Leak Itself
The breach became widely known after files associated with AIO-TLP370 were post on TheJavaSea.me, a site infamous for hosting leaks and unauthorized data dumps. Reports indicate that the leaked package was large—over 1 GB in size—and containe a variety of highly sensitive materials, including:
- Source Code for core log processing functionalities.
- Configuration Files revealing system settings and operational parameters.
- Hardcoded API Keys and Credentials embedded directly in scripts.
- Incident Response Playbooks detailing how the system handles breaches and alerts.
- Developer Notes and Roadmaps providing insight into planned updates and system architecture.
The presence of both technical documentation and operational keys greatly increases the risk level of this leak.
Potential Consequences
The fallout from this type of leak can be significant. For one, having access to the source code allows malicious actors to reverse-engineer the system, search for flaws, and develop highly targeted exploits. Additionally, exposed API keys can give unauthorized users direct access to systems connected to cloud platforms or secure databases.
Some of the most concerning potential outcomes include:
- System Compromise – Attackers could infiltrate networks that use AIO-TLP370.
- Credential Abuse – Stolen keys and passwords may be used for unauthorized transactions or server access.
- Operational Exposure – Internal security strategies revealed in playbooks can help hackers bypass defenses.
- Long-Term Security Risks – Even if immediate patches are applied, knowledge of system design remains in the hands of potential attackers.
Why This Leak Matters
This incident isn’t just about one platform or one company—it’s a reminder that security begins with prevention, not reaction. Even the most advanced security systems can be compromised if sensitive data is not handled with strict control measures.
It also highlights the growing problem of leak-sharing platforms, which make it easy for stolen data to be distributed quickly and globally. Once such information is public, it is nearly impossible to contain.
Recommended Actions for Organizations
In the wake of the AIO-TLP370 breach, cybersecurity experts suggest the following measures:
- Conduct Full Security Audits – Identify and patch any vulnerabilities that could be exploited using leaked information.
- Rotate All Credentials – Replace all API keys, passwords, and authentication tokens associated with the leaked files.
- Apply Urgent Updates – Deploy patches for software components that may be affected.
- Segment Networks – Restrict access to critical systems and logs.
- Review and Update Incident Response Plans – Ensure teams know exactly how to react to similar threats in the future.
Looking Ahead
While the AIO-TLP370 leak is troubling, it serves as a valuable case study for both IT security teams and organizations at large. It underlines the importance of constant vigilance, secure coding practices, and responsible data handling. The speed at which such leaks spread means that companies cannot afford to take a “wait and see” approach—they must respond instantly and comprehensively.
Quick Summary
Conclusion
The TheJavaSea.me AIO-TLP370 leak is more than just another entry in the long list of digital breaches; it is a stark reminder of the real-world consequences when sensitive technical infrastructure is exposed. Whether you are a developer, a systems administrator, or a business leader, the lessons from this event are clear—protect your systems, secure your data, and always assume that breaches are a matter of “when,” not “if.”